Please create good tiktok(-analyse)s
Once again a report about TikTok is going around. We have read it carefully: It’s mostly nonsense. Let’s have a look at the claims one after the other
A shocking new report today outlines just how far TikTok goes to harvest personal data from its users, data that some fear could be used by China for intelligence and cyber hacking. #TheProjectTV pic.twitter.com/cHkR1bwTdK
— The Project (@theprojecttv) July 18, 2022
- To promote the report, the analysis company says, among other things: “TIKTOK IS NOT COMPATIBLE WITH OUR APPROACH TO PRIVACY”. Oh really? To get the report, you have to provide your first name, phone number and email address. Exciting “approach to privacy”… 🤔
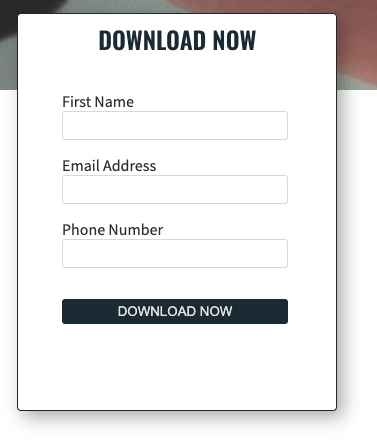
Download form with request for First Name, Email Address and Phone NumberDownloadformular mit Abfrage von First Name, Email Address und Phone Number
To keep your data protected, you can also read the report in the Internet Archive: https://archive.org/details/tik-tok-technical-analysis-17-jul-2022.-media-release #ServiceTweet
- User Permissions and Third-Party Data Access
Here they automatically generated a list of all permissions that the TikTok app can get:
List of permissions on Android: read and write external storage, access coarse location, authenticate accounts, camera, get tasks, read calendar, read contacts, record audio, system alert window, write calendar List of permissions on ios: access apple media library, access calndars, access the camera, access contacts, access location inforamtion when app is in the foreground, access microphone, access the users photo library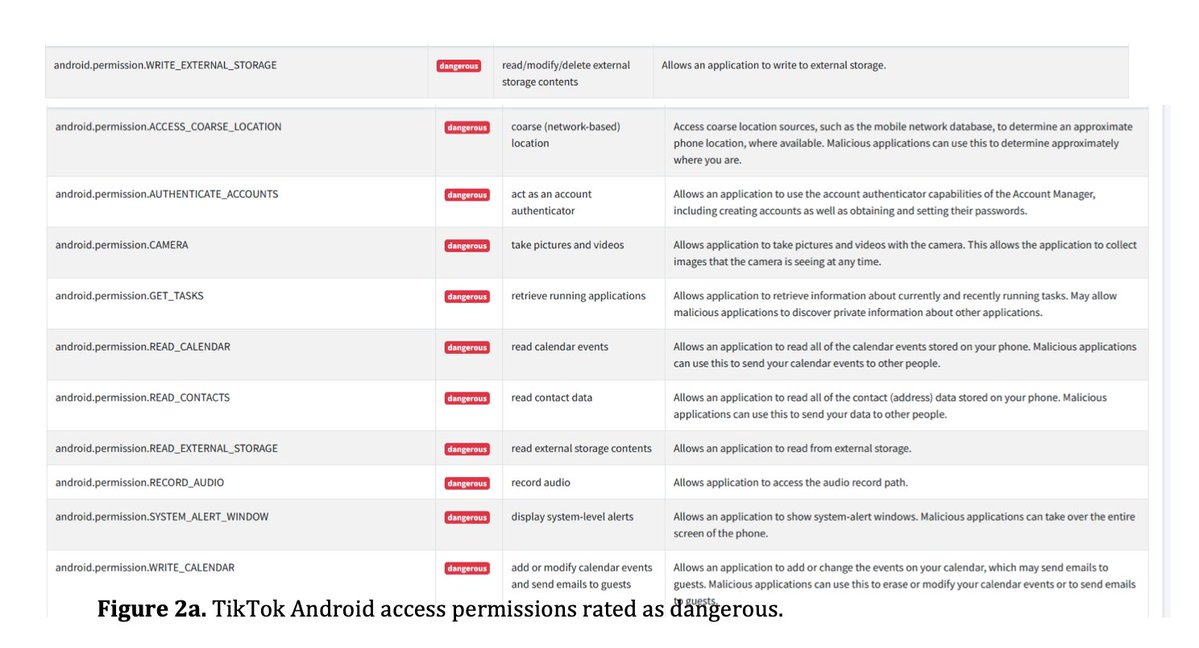
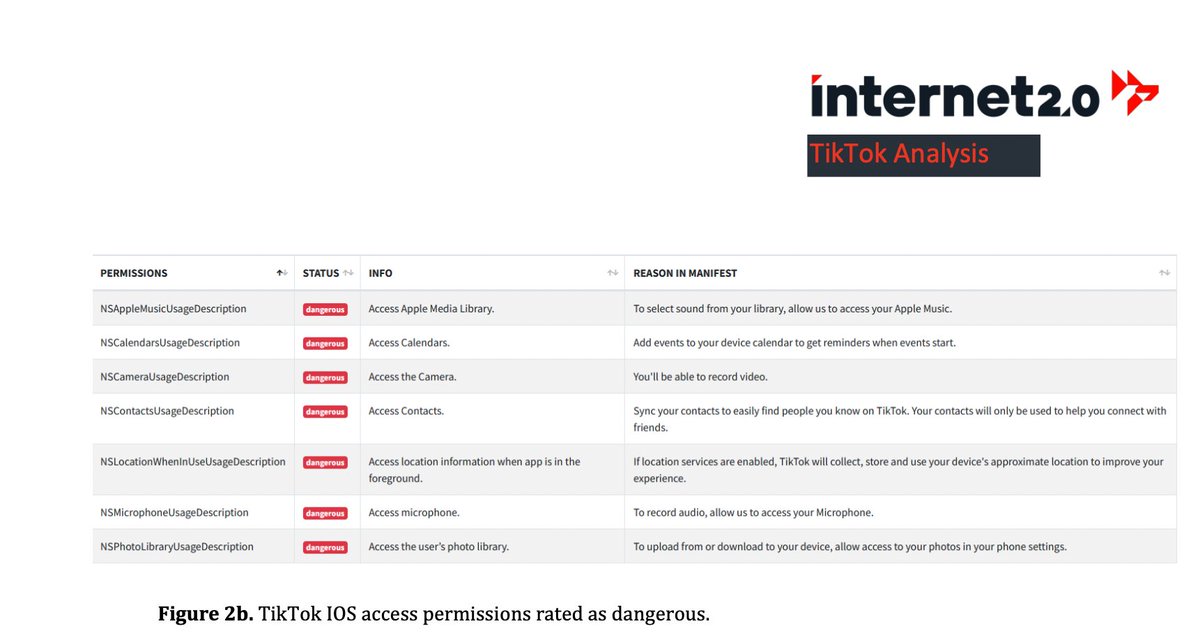
Two things are important for this:
- Most of these permissions have to be explicitly confirmed by the users again. You probably know the “Allow access to contacts?” dialog.
- For (almost) all of them it is quite easy to explain why TikTok needs this:
Camera & Audio recording: Well, it’s a video app. Calendar: you can have livestreams added to your calendar Contacts: You can find people from the address book Photo access: You can use pictures from the photo gallery in the videos
The report wrongly says that the app asks for access to contacts in an endless loop if you deny it. This is not true: although the app asks every now and then during use, you can always refuse and continue using the app without any problems.
For other permissions, there is even less evidence: Here, the “analysts” claim with reference to screenshots that these permissions are maliciously exploited. But the screenshots do not show that at all.

Here they just added wild annotations to code snippets - without it being clear if and when this part of the code is ever used. More context would be required to proof that: either a longer argument on the source code, or by showing malicious behavior while the app is running.
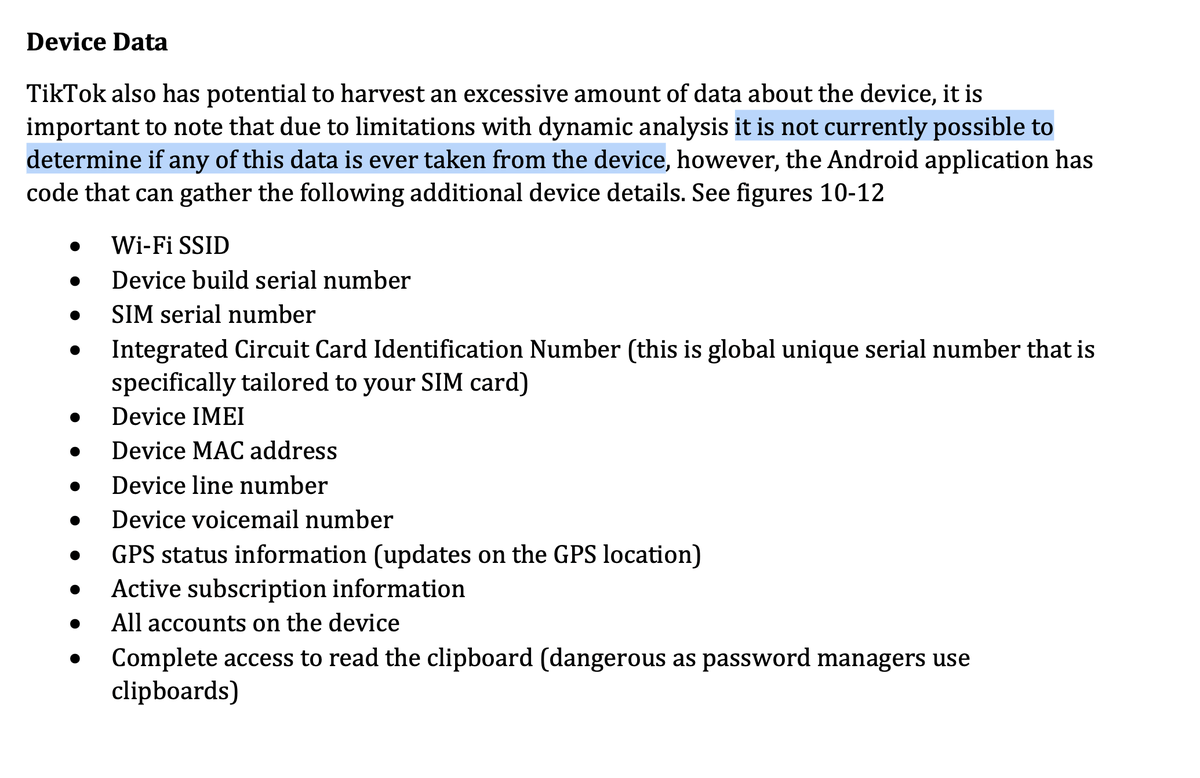
- Device and user data harvesting
Here the report itself states that the analysis was not accurate enough to prove anything. But of course they still claim it 🤷🙃
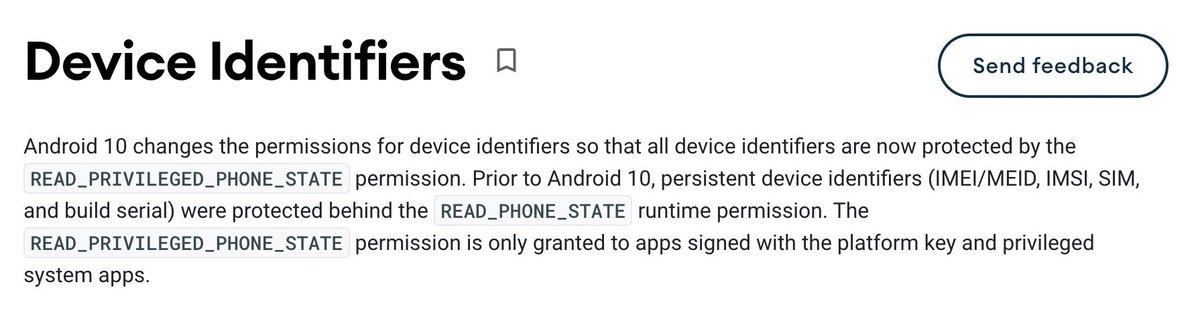
To retrieve some of this data, the app would need additional permissions - which it neither has nor wants to get: For IMEI, IMSI, SIM/build serial number and others, you need the permissions “READ_PHONE_STATE” or “READ_PRIVILEGED_PHONE_STATE”.
https://source.android.com/devices/tech/config/device-identifiers
- Connections to mainland China
Here the report lacks any depth to be able to judge what this means. From a technical point of view, it is nonsense to try to determine the location of servers based only on an IP address - without insight into the hoster’s infrastructure.

CD-Cover: ‘The three investigators and the mysterious IP’. A green gloing phone with the flag of china, whichs shadow shows the TikTok-Logo
The company to which the IP allegedly belongs offers cloud solutions in general: https://intl.baishancloud.com/ Just with the information about the IP, one cannot conclude where the servers are located, what TikTok uses them for, who actually gets data, etc.
- Conclusion
The report lacks technical depth and meaningful information. Most of the output of automatic tools has been regurgitated without question. That does not make an analysis. These tools only provide hints, which places should be looked at more closely.
But it needs again a lot of manual work to analyze and evaluate the found places exactly. For fun, we uploaded a privacy-friendly email app to one of these scanners and had it analyzed. This was the result:

App Security Score: 29/100 (CRITICAL RISK) – Grade: F
It is a problem that reports are published in this form, because the report is not aimed at a technical audience that can see the flaws directly, but at “policy makers and legislators to make evidence-based decisions”.

Screenshot der Executive Summary: ‘This report is for policy makers and legislators to make evidence-based decisions’
And those can’t generally be assumed to get through it technically. Instead, the inflated claims stick and influence decisions. Such things also lead to such strange moves as Trump’s TikTok ban. Big media outlets would be in duty to critically check such claims instead of taking them directly with a clickbaity headline.
Of course we have to criticise TikTok! All the more important are good analyses of the problems - from security gaps to data protection violations to the business model. Because these enable a social discourse - misleading pseudo-“analyses” harm it.
By the way, the authors of this report are not unknown: Already 2 years ago they published an equally questionable report as “Penetrum” and also had big media outlets jumping on it.
Transparency note: We also use TikTok. Follow us at https://tiktok.com/@zerforschung